Nowhere is the creativity of advertising more clearly displayed than in a medium that generates positive associations between customers and brand. Posters rely less on conversions and more on raising awareness. You’re attempting to occupy the mental territory overlaid upon a city through landmarks encased in snap frames and good will. Knowing where to display a poster, and how to structure it so that your brand is registered in a split-second, is key to its success. Figures from the OAAA show that outdoor advertising is the fastest...
You Are Browsing ‘How-To’ Category
Phone unlocking is a subject plagued by images of dodgy street-corner shops with flashing neon lights. However, over the years and since it was legal to do back in 2001 (and quite rightly) phone unlocking has changed dramatically. You can now order an unlock code online and within 5 minutes you have the exact same code that your network would take up to 30 days to send with best part that all for cheaper as well. The subject in itself confuses people, partly because they just don’t understand. I’m often asked questions such as, can...
Expansion is a significant sign of business growth. Once business owner decides to expand, it means the firm receives overwhelming cash flow. Business expansion enables the enterprise to serve or cater to a larger number of consumers. Thus, the investment might come back twice or multiple times letting the business grow even more and more. Are you on a lookout to expand your business? It is pretty simple to think of the expansion itself and how it will bring more profit to the business. However, business expansion is a very challenging...
Today, Ecommerce business is a juicy target for hackers. Hackers have stolen an estimated $1 trillion in intellectual property. A research says “every ecommerce business was attacked in the five month timing period”. 80% of companies experiences minimum one major network attack per month. Each successful attack averages 500,000 American dollars. Hackers and your Vulnerable Shopping Cart: The invention of shopping cart software has made customer’s shopping experiences quick and easy. It has also sparked the interest of many hackers....
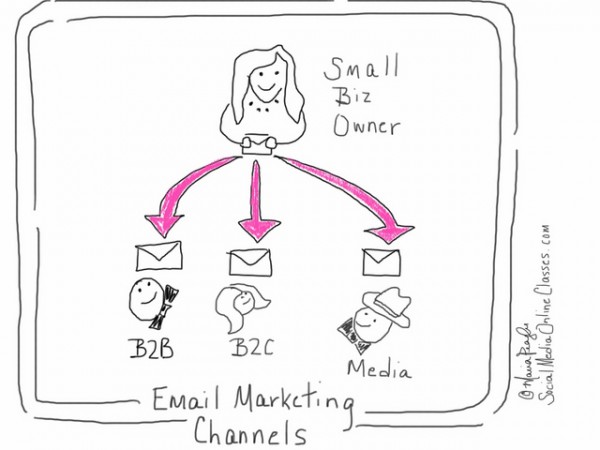
Over the last several years, social media sites have skyrocketed in popularity, with these digital gathering places attracting users of all ages and interests across the world. As soon as it became evident that such sites were more than merely a passing fad, advertisers arrived in droves as well. While social media is still a hot topic in marketing circles, it actually isn’t the most important medium for marketing on the Internet. In reality, a more familiar — some might say classic — method of Internet marketing is...
Until recently, the job of the affiliate marketer was one that was focused almost exclusively on websites and email lists. The conversion pathway from search-engine to purchase was simple and predictable. Users would land on a squeeze page, and then, depending on the keywords that sent them there, either open up their wallets or their email inboxes after being wowed by they saw on your site. Things have changed a lot in recent years. Websites are bigger and more complex, users expect more from every website they visit, and social media...
The Significance Of After-school Education In Modern, Technologically Driven Society Project management refers to the process of using knowledge, skills, techniques and tools to plan, organize, staff, direct, and control the production of a given system. A proper project management approach is a comprehensive description of an organized and logical method, and PRINCE2 is one of the best examples of a properly structured project management approach that may be tailored for any type of project. What is PRINCE2? PRINCE, which is the short...
Why CC Security? If you are tech-savvy and are up to date with the latest buzz going on in the techno realm then you surely have heard of CC security. CC security stands for Common Criteria, which is a standard security system used by software companies to verify that particularsoftware has undergone all the tests and fulfills the specifications that make it fit for personal use. The CC security system has been deemed as highly desirable by major organization and even government agencies. The merits of this security system is further...
Hypervisor vs. Container Since virtualization is becoming increasingly prevalent in the home users, an auspicious introductory article to this domain becomes more necessary than ever. What is virtualization exactly? In simple terms, virtualization is a method that allows the running of one or more “computers” on a single hardware platform, or even easier, two different operating systems on a single PC. For example, a PC can run both a Windows and a Linux OS, or a Windows 98 installation as well as an XP one. A more complex explanation...
The key to training your brain is to keep it active. Watching TV is not going to stimulate your brain enough in order to keep it active. Playing computer games can be helpful, but it really depends upon the game you are playing. The ones that take persistence are often the better ones. It has also been shown that the ones that scare you will often activate your mind in a way that is hard to recreate indoors. All you need to do is keep your mind active in some way, and your brain will train itself. Here are seven ways you can keep your...